Nachdem ich mein Mailsystem von Amavis und Spamassassin auf Rspamd umgestellt habe, möchte ich nun ClamAV als Virenscanner hinzuführen. Nachfolgend die Schritte zur Konfiguration.
Damit Rspamd sich mit ClamAV verbinden kann muss die ClamAV Gruppe auf Rspamd berechtigt werden.
# usermod -a -G clamav _rspamd
# chown -R clamav:clamav /var/run/clamavAls nächstes wird die ClamAV Konfiguration erweitert und folgendes hinzugefügt, bzw. geprüft:
# nano /etc/clamav/clamd.conf
PidFile /var/run/clamav/clamd.pid
LocalSocket /var/run/clamav/clamd.ctl
TCPSocket 3310
TCPAddr localhost
# https://betatim.github.io/posts/clamav-memory-usage/
ConcurrentDatabaseReload noClamAV Dienst neustarten
# service clamav-daemon restartClamAV Log prüfen
# cat /var/log/clamav/clamav.log |grep 3310
Sun Mar 6 21:36:08 2022 -> TCP: Bound to [::1]:3310
Sun Mar 6 21:36:08 2022 -> TCP: Bound to [127.0.0.1]:3310
# cat /var/log/clamav/clamav.log |grep socket
Sun Mar 6 21:36:08 2022 -> LOCAL: Unix socket file /var/run/clamav/clamd.ctl
Diese Ports werden für Rspamd und ClamAV benötigt.
# egrep "3310/tcp|1133./tcp" /etc/services
clamd 3310/tcp
rspamd-proxy 11332/tcp
rspamd-worker 11333/tcp
rspamd-controller 11334/tcp
rspamd-fuzzy 11335/tcpPrüfen der Ports
# netstat -unplet|egrep "rspamd|clamd"
tcp 0 0 127.0.0.1:3310 0.0.0.0:* LISTEN 114 567159319 18138/clamd
tcp 0 0 127.0.0.1:11332 0.0.0.0:* LISTEN 124 563882212 7228/rspamd: rspamd
tcp 0 0 127.0.0.1:11333 0.0.0.0:* LISTEN 124 563882224 7230/rspamd: normal
tcp 0 0 127.0.0.1:11334 0.0.0.0:* LISTEN 124 563882218 7229/rspamd: contro
tcp6 0 0 ::1:3310 :::* LISTEN 114 567159318 18138/clamd
tcp6 0 0 ::1:11332 :::* LISTEN 124 563882213 7228/rspamd: rspamd
tcp6 0 0 ::1:11333 :::* LISTEN 124 563882225 7230/rspamd: normal
tcp6 0 0 ::1:11334 :::* LISTEN 124 563882219 7229/rspamd: contro
ClamAV für Rspamd konfigurieren
Nun die Konfiguration für Antivirus in Rspamd wie folgt anpassen.
# nano /etc/rspamd/local.d/antivirus.conf
servers = "127.0.0.1:3310";
#servers = "/var/run/clamav/clamd.ctl";Dienst Rspamd neustarten
# service rspamd restartRspamd Log überprüfen
# cat /var/log/rspamd/rspamd.log | grep clamav
2022-03-05 23:55:58 #17221(main) <rpncc6>; lua; antivirus.lua:185: added antivirus engine clamav -> CLAM_VIRUSISPconfig Rspamd Template
# nano /usr/local/ispconfig/server/conf-custom/install/rspamd_antivirus.conf.master
#######################################################################################
# ISPConfig:
# vi /usr/local/ispconfig/server/conf-custom/install/rspamd_antivirus.conf.master
# ispconfig_update.sh --force
#######################################################################################
clamav {
# If set force this action if any virus is found (default unset: no action is forced)
action = "reject";
# Scan mime_parts separately - otherwise the complete mail will be transferred to AV Scanner
scan_mime_parts = true;
# Scanning Text is suitable for some av scanner databases (e.g. Sanesecurity)
scan_text_mime = true;
scan_image_mime = true;
# If `max_size` is set, messages > n bytes in size are not scanned
#max_size = 20000000;
# symbol to add (add it to metric if you want non-zero weight)
symbol = "CLAM_VIRUS";
# type of scanner: "clamav", "fprot", "sophos" or "savapi"
type = "clamav";
# For "savapi" you must also specify the following variable
#product_id = 12345;
# You can enable logging for clean messages
log_clean = true;
# servers to query (if port is unspecified, scanner-specific default is used)
# can be specified multiple times to pool servers
# can be set to a path to a unix socket
# Enable this in local.d/antivirus.conf
servers = "127.0.0.1:3310";
#servers = "/var/run/clamav/clamd.ctl";
# if `patterns` is specified virus name will be matched against provided regexes and the related
# symbol will be yielded if a match is found. If no match is found, default symbol is yielded.
patterns {
# symbol_name = "pattern";
JUST_EICAR = "^Eicar-Test-Signature$";
}
patterns_fail {
# symbol_name = "pattern";
CLAM_PROTOCOL_ERROR = '^unhandled response';
}
# `whitelist` points to a map of IP addresses. Mail from these addresses is not scanned.
whitelist = "/etc/rspamd/antivirus.wl";
}ISPconfig Dienste neukonfigurieren
# ispconfig_update.sh --force
...
Reconfigure Services? (yes,no,selected) [yes]: yes
The following custom templates were found:
/usr/local/ispconfig/server/conf-custom/install/rspamd_antivirus.conf.master
Do you want to rename these conf-custom templates now so the default templates are used? (yes,no) [no]: no
...Rspamd Antivirus Konfiguration prüfen
# egrep -v '(^.*#|^$)' /etc/rspamd/local.d/antivirus.conf
clamav {
action = "reject";
scan_mime_parts = true;
scan_text_mime = true;
scan_image_mime = true;
symbol = "CLAM_VIRUS";
type = "clamav";
log_clean = true;
servers = "127.0.0.1:3310";
patterns {
JUST_EICAR = "^Eicar-Test-Signature$";
}
patterns_fail {
CLAM_PROTOCOL_ERROR = '^unhandled response';
}
whitelist = "/etc/rspamd/antivirus.wl";
}Test Rspamd und ClamAV mit Eicar Testvirus
Download Eicar Testvirus
# wget https://secure.eicar.org/eicar.com --no-check-certificate && gzip eicar.comMail aus der Konsole mittels swaks, dem “Swiss Army Knife for SMTP” Tool, senden.
# apt install -y swaksSenden der Mail mit Eicar Testvirus im Anhang
# swaks --to receiver@domain.tld --from sender@doamin.tld --attach - --server localhost < eicar.com.gzRspamd Log prüfen
# cat /var/log/rspamd/rspamd.log | grep -i eicar
2022-03-06 21:58:09 #23152(normal) <0510b8>; lua; common.lua:110: clamav: result - virusfound: "Eicar-Test-Signature - score: 1"
...prüfen des ClamAV Log
# cat /var/log/clamav/clamav.log |grep -i found
Sun Mar 6 21:58:09 2022 -> instream(127.0.0.1@58828): Eicar-Test-Signature(d3c03a1d552e6b7eed704e6e24d7b9d7:98) FOUNDSyslog prüfen
# cat /var/log/syslog |grep -i eicar
clamd[23158]: Sun Mar 6 21:58:09 2022 -> instream(127.0.0.1@58828): Eicar-Test-Signature(d3c03a1d552e6b7eed704e6e24d7b9d7:98) FOUND
postfix/cleanup[24501]: 2DC19A219AA: milter-reject: END-OF-MESSAGE from localhost[::1]: 5.7.1 clamav: virus found: "Eicar-Test-Signature"; from=<sender@domain.tld> to=<receiver@domain.tld> proto=ESMTP helo=<mailserver.tld>Rspamd WebUI History
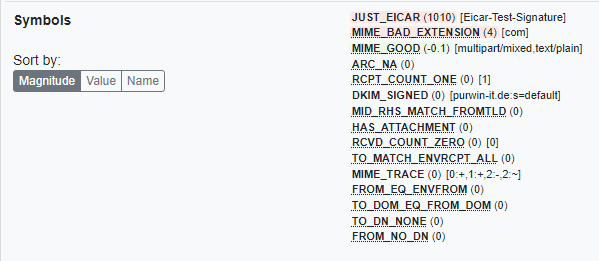
Thats it .. Have Fun!
Interessiert in verschiedenste IT Themen, schreibe ich in diesem Blog über Software, Hardware, Smart Home, Games und vieles mehr. Ich berichte z.B. über die Installation und Konfiguration von Software als auch von Problemen mit dieser. News sind ebenso spannend, sodass ich auch über Updates, Releases und Neuigkeiten aus der IT berichte. Letztendlich nutze ich Taste-of-IT als eigene Dokumentation und Anlaufstelle bei wiederkehrenden Themen. Ich hoffe ich kann dich ebenso informieren und bei Problemen eine schnelle Lösung anbieten. Wer meinen Aufwand unterstützen möchte, kann gerne eine Tasse oder Pod Kaffe per PayPal spenden – vielen Dank.

Danke, dass auch solche Themen – teils in der Tiefe – behandelt werden.
Um auch Eindrücke von Alternativen wie rspam zu erhalten.
Gruß
Hi Craft,
ja gerne, wenn nur mehr Zeit wäre, dann würde ich gerne noch weiter in die Tiefe gehen :).